Smartwatch adoption is on the rise, but Hewlett-Packard warns the wearable devices that store personal health and financial information do not have enough security functions.
HP conducted a study on 10 popular Android and Apple smartwatches and their respective mobile applications to assess security vulnerabilities, as part of an ongoing study looking at Internet of things security.
The report does not state which 10 watches were tested in the study, only that each had an iOS or Android mobile application with it. This will include the Apple Watch and possibly the Samsung Gear Live, the Asus Zenwatch, the Sony SmartBand Talk, the LG G Watch, and the Moto 360, among others.
The study conducted by HP Fortify, the company's security division, found all of the tested smartwatches contain significant vulnerabilities, including insufficient authentication, lack of encryption and privacy concerns.
The security division used its product Fortify on Demand to test the vulnerabilities. This included standard testing techniques that combine manual testing and verification along with automated scanning technology. Devices and their components were assessed based on the OWASP Internet of Things Top 10 and the specific vulnerabilities associated with each category.
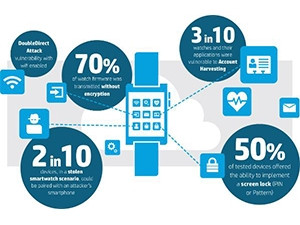
Key findings show:
* There is DoubleDirect (a 'man-in-the-middle' attack, specifically targeted at iOS, Android and Mac users) vulnerability with WiFi enabled.
* 70% of watch firmware was transmitted without encryption.
* Two in 10 devices in a stolen smartwatch scenario could be paired with an attacker's smartphone.
* Three in 10 watches and their applications were vulnerable to account harvesting.
* 50% of tested devices offered the ability to implement a screenlock (PIN or pattern).
* Data collected initially on the watch and passed through to an application is often sent to multiple backend destinations (often including third parties).
* Watches that include cloud interfaces often employed weak password schemes, making them more susceptible to attack.
* Watch communications are trivially intercepted in 90% of cases.
* Smartwatches that included a mobile application with authentication allowed unrestricted account enumeration.
* The combination of account enumeration, weak passwords, and lack of account lockout means 30% of watches and their applications were vulnerable to account harvesting, allowing attackers to guess login credentials and gain access to the user's account.
"Smartwatches have only just started to become a part of our lives, but they deliver a new level of functionality that could potentially open the door to new threats to sensitive information and activities," says Jason Schmitt, HP Fortify GM.
"As the adoption of smartwatches accelerates, the platform will become vastly more attractive to those who would abuse that access, making it critical that we take precautions when transmitting personal data or connecting smartwatches into corporate networks."
Recommendations
HP concludes the report by saying smartwatches will likely become more and more part of everyday life, allowing users to perform everyday tasks like unlocking their car or paying for groceries. This will leave sensitive information vulnerable to attack because of the way smartwatches are manufactured.
HP recommends smartwatch wearers:
* Do not enable sensitive access control functions (car or home) unless strong authentication is offered (ie, two-factor).
* Enable passcode functionality to prevent unauthorised access to data, opening of doors, or payments on behalf of the wearer.
* Enable security functionality (ie, passcodes, screen locks, two-factor and encryption).
* Ensure strong passwords are used for any interface such as mobile or cloud applications associated with the watch.
* Do not approve any unknown pairing requests.
HP recommends enterprise technical teams:
* Ensure implementations of Transport Layer Security ? a protocol that ensures privacy between applications and users on the Internet ? are configured and implemented properly.
* Protect user accounts and sensitive data by requiring strong passwords.
* Implement controls to prevent man-in-the-middle attacks.
* Build mobile applications (specific to each ecosystem) into the device.
Share