
The first viruses infiltrated personal computers over 25 years ago; it's been more than a decade since the earliest iterations of malicious software made their way onto our smart devices. As technology has evolved, so too have the risks. Mobile devices present a myriad of these.
"Mobility is not a trend that will disappear," says Riaan Badenhorst, MD at Kaspersky Lab Africa. "The more devices you use, the more your digital presence grows, which presents cyber criminals with more opportunities to target you. While mobile devices have made various elements of our lives more convenient, we must always remember that this convenience comes at a price, he adds. "We all seem to remember to download security solutions on our desktop computers or laptops, but for some reason, when it comes to our phones, we don't really think about these being targeted by cyber criminals. As a result, most of us tend to lack the necessary precautionary mobile security measures."
Mobile devices are constantly evolving, the amount of data being generated has increased exponentially and the rate of development of new applications has skyrocketed. All of these factors have changed the security game, says Kevin McKerr, senior security specialist at IBM SA. "This velocity and volume requires a different, risk-based approach to security. Businesses need automated and role-based access controls that are smart enough to know where the user is located, what they want to do, and what normal behaviour is before letting them in the door." A diverse portfolio of security solutions to meet each organisation's individual needs is a must. "These solutions deliver a protective layer of security intelligence for correlating events across the enterprise and facilitating proactive responses. This way, organisations can help prevent identity theft, reduce the risk of fraud and protect all types of critical data," notes McKerr.
What's frightening, says Greg Griessel, consulting systems engineer for security solutions at Cisco SA, is the increased sophistication of tactics developed by malware authors and online criminals in recent years. They adapt and innovate rapidly and are quick to enhance their capacity to compromise systems and evade detection, he continues. Despite this, many organisations are unaware of the major business disruptions that could result from a security breach and remain unprepared to respond should something go wrong. The ever common disconnect between business and IT means that CEOs fail to pay sufficient attention to cyber security and regard mobile defence as an afterthought. "However, as cyber-attacks increase in frequency, CEOs and employees are now forced to take cyber security seriously," he says. And this increased caution needs to be happening at all levels; everyone from top-level business and IT all the way down to employees must understand their role in safeguarding against harmful hacks.
Widening the net
It wasn't long ago that an organisation only needed to worry about employees accessing a few, highly controlled and contained applications on private networks, adds McKerr. Fast forward a few years and there are potentially millions of users coming into systems to access their records - from varying groups of staff members to users who are not employees, to customers, partners and contractors.
In line with this, Badenhorst cites mobility, the use of personal devices at work (BYOD) and social media in the workplace as the three biggest concerns for IT managers.
Employee behaviour is therefore the deciding factor in whether BYOD will succeed or fail.
But these threats, coupled with near ubiquitous device proliferation, present a surprising opportunity when it comes to fraud prevention, adds Michelle Beetar, MD of Experian. The more consumers and businesses conduct activities using online portals and the more they interact with other mobile devices, the easier it is to identify distinctive patterns around user behaviour. "This intelligence becomes richer as the number of devices and online interactions grows, creating a powerful new way to identify and secure legitimate users and expose criminals. This takes advantage of historical patterns of behaviour between vast numbers of devices, as well as key device-based indicators of risk, such as a large number of accounts associated with a single device." The trick to getting your security strategy right is to find a happy balance between putting stringent enough controls in place while still providing a satisfying user experience, she points out. "In a world where people are increasingly reliant on a variety of internet-connected devices for everything from banking to shopping to booking travel, preventing online fraud and creating friction-free customer experiences is a constant and complex business challenge," she says.

And companies can no longer plead ignorance when a security threat or breach occurs, says Anzelle Robertson, legal and compliance officer at Oxygen8 SA. She describes compliance as being key to conducting sustainable business. "Organisations are more likely to attract customers if they can proactively prove their compliance with national legislation and local regulations."
Brainstorming BYOD
Just like all new technology trends, there are very real security concerns that need to be addressed before a BYOD programme can be successful, says Badenhorst.
From an IT perspective, the biggest threats around BYOD are risk and control, states Michael Morton, the mobile security specialist at managed security services vendor Securicom. He believes that the days when IT could limit an employee's use of a standard mobile device to only facilitating the sending and receiving of corporate e-mail are no more. However, he notes that the benefits of BYOD - including increased productivity and reduced hardware costs, among others - make it a worthwhile strategy to get right. "With a BYOD strategy in place, employees are provided with tools to better their productivity on devices they love and know. IT still has control if there is a well-defined and well implemented BYOD strategy." A lacklustre strategy could see malicious software infecting organisation networks, data breaches occurring due to the loss or theft of a device and the inadvertent installation of apps and software that compromises compliance and security.
End-user training and educating employees about why their behaviour may be problematic is an underutilised method to guard against security threats, says Morton, noting that this can be a more effective strategy than hoping IT will be poised to respond when end-users make a bad decision. It often proves most difficult to protect employees against themselves, he continues.
This velocity and volume requires a different approach to security, a risk-based approach.
Badenhorst agrees. Security attacks have become a fact of life and training employees to understand that they are liable to protect the organisation and themselves is essential. Cyber criminals have identified people as the weakest link in the security chain and will target them, he adds. "Employee behaviour is therefore the deciding factor in whether BYOD will succeed or fail." Any truly effective BYOD policy must go beyond implementing basic anti-malware protection and should include software to remotely remove data from a device should it permanently go missing.
Having a correctly implemented BYOD strategy in place is beneficial for both employer and employee, stresses Morton. "At the end of the day, what it comes down to is business wanting their employees to be more productive, giving employees the freedom of choice when selecting mobile devices and IT still having control over who is allowed to access corporate information, what corporate information is being accessed and having insight into the mobile environment."
Mastering MDM
Mobile device management (MDM) is the administration, deployment, monitoring and securing of mobile devices such as smartphones and tablets. It's the key to finding a balance between corporate productivity and employee privacy, while also ensuring that an organisation is audit-compliant.
As such, most companies want to make use of an MDM solution, but when questioned about their MDM policies, many are clueless, says Michael Morton, of managed security services vendor Securicom. He believes our smartphones are as valuable as our wallets and ID books because they house so much personal information, information that criminals are able to exploit. But employees are often hesitant to install an MDM profile onto their device. "Failing to define your MDM policy is the biggest mistake business is making." IT and business need to sit down together and discuss what level of access is required for different departments within the organisation. And only once these access requirements have been determined, can IT select the best MDM policy to meet their unique needs.
Security stats
Some of the highlights from the 2015 CISCO Midyear Security Report include:
* Exploits of Adobe Flash vulnerabilities are on the rise. Widely used exploit kits include Angler and Nuclear.
* Digital economies and the Internet of Everything (IoE) have created new opportunities for adversaries.
* Operators of crime ware, like ransomware, are hiring and funding professional development teams to ensure they remain profitable.
* Criminals are turning to anonymous web networks like Tor and the Invisible Internet Project (I2P) to relay command-and-control communications, while evading detection.
* Microsoft Office macros are once again being used to deliver malware.
* Text from Jane Austen's classic novel Sense and Sensibility is occasionally incorporated into web landing pages that host malicious software. After reading this content, most antivirus and security solutions will categorise these pages as legitimate.
* Spam volumes are increasing in the US, China and the Russian Federation, but remained stable across other regions in the first half of 2015.
* The security industry is paying more attention to mitigating vulnerabilities in open-source solutions.
* Exploits involving Java are on the decline.
The local picture
When we hear stories about phone hacks, secret government surveillance and elaborate viruses, South Africans tend to think that this kind of thing only really happens abroad. But this is most certainly not the case, says Michael Morton, mobile security specialist at Securicom. In 2013, South Africa was ranked fifth in terms of total global security incidents. South Africa is also the second most targeted country in the world for phishing attacks and internet fraud. "Being at the southern point of Africa does not mean we are out of harm's way. Our devices are still at risk," says Morton.
Online privacy
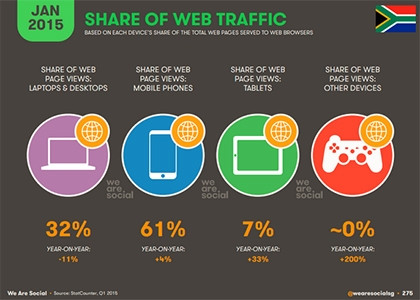
Of the 24.9 million active internet users in SA, 61 percent are accessing web pages from their mobile devices, a trend that can been seen across all nine provinces. While only 12.6 percent of South African households have access to both a mobile device and a landline, 83.1 percent have access to a mobile device. "What this tells us is that when it comes to accessing the internet, South Africans are making use of their mobile devices. And with mobile devices being the primary means of internet access, it's safe to conclude that our biggest security exploits will be on these devices," notes Morton.
Local businesses and consumers are becoming more and more aware of this fact, according to Riaan Badenhorst, MD at Kaspersky Lab Africa. The recent Consumer IT Security Risks Survey 2015 highlighted that the number of internet users who are concerned about their online privacy increased significantly between 2014 and 2015. Some 82 percent of users in SA are concerned that someone could gain access to their personal files, he continues. Just over half of the suvey participants are worried that there may be programmes on their devices secretly collecting information about them, and 49 percent do not trust their own webcams as these can be used to spy on device owners. "All of these concerns make it vital that security solutions find new ways to ensure user privacy on mobile devices," Morton concludes.
Mobile security and your customers
Any organisation processing personal information is bound by the Protection of Personal Information Act (POPI). While you may not think that this is a priority for your business, merely having a database with the mobile phone numbers of your customers is classed as `processing personal information' under POPI, says Anzelle Robertson from Oxygen8 South Africa.
According to Robertson, the Wireless Application Service Providers Association (WASPA) acts as the local regulatory body for wireless application service providers or WASPs. The association's Code of Conduct details the procedures and obligations that organisations have to adhere to in order to protect mobile consumers. The importance of mobile security and of this kind of body was particularly evident at the beginning of this year when many WhatsApp users fell victim to a scam spread via the platform, notes Robertson. Users were sent an SMS asking them to update WhatsApp add-ons and providing a link to do so. The criminals were able to fleece people for money by tricking WhatsApp users into agreeing to allow the service to deduct R7 per day from their phone bill, which when left unnoticed, cost some R200 in a single month.
Consumer education
In this scenario, says Robertson, distracted or ignorant consumers failed to notice the pricing information that, according to regulatory requirements, should always be placed immediately adjacent to the button that initiates the next step in any sign-up process. "This is important so that consumers are well aware of the amount they are paying. It can't be hidden away at the bottom of the page. And this is how criminals catch people." Despite this scenario, she believes that the regulatory climate has various procedures in place to ensure consumers are protected. Consumer education around terms and conditions, pricing and support services is essential, Robertson notes.
Regulations also ensure that consumers must confirm any subscription service requests and be informed of any new services they have subscribed to in order to ensure that they are aware of what is being billed to their account. The consumer is well protected under these regulations, but it's still possible for them to be hoodwinked into signing up for something they don't really need or want. "Slow down and carefully read the text before clicking the `next' or `accept' buttons," she advises.
Share