Cape Town, 28 Mar 2017

Hackers are constantly trying to find new ways to bypass cyber security efforts, sometimes turning to older, almost forgotten, methods to gain access to valuable data. Researchers at PandaLabs, Panda Security's anti-malware research facility, recently detected a targeted attack that did not use malware, but rather used scripts and other tools associated with the operating system itself in order to bypass scanners.
Using an attack method that has gained popularity recently, the hackers launched a brute-force attack against the server with the Remote Desktop Protocol (RDP) enabled. Once they have access to the log-in credentials of a device, the intruders gain complete access to it.
At this stage, the attackers run the seethe.exe file with the parameter 211 from the computer's Command Prompt window (CMD) - turning on the 'Sticky Keys' feature.
Next, the hacker initiates Traffic Spirit - a traffic generator application that ensures the attack is lucrative for the cyber criminals.
Once this is complete, a self-extracting file is launched that uncompresses the following files in the %Windows%\cmdacoBin folder:
* registery.reg
* SCracker.bat
* sys.bat
The hacker then runs the Windows registry editor (Regedit.exe) to add the following key contained in the registery.reg file:
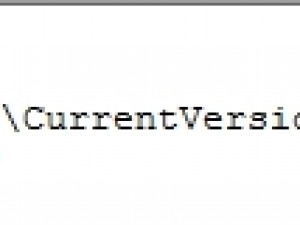
This key aims at ensuring that every time the Sticky Keys feature is used (sethc.exe), a file called SCracker.bat is run. This is a batch file that implements a very simple authentication system. Running the file displays the following window:

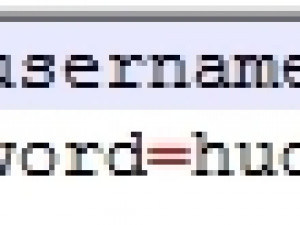
The user name and password are obtained from two variables included in the sys.bat file:
This creates a backdoor into the device through which the hacker gains access. Using the backdoor, the hacker is able to connect to the targeted computer without having to enter the log-in credentials, enable the Sticky Keys feature, or enter the relevant user name and password to open a command shell:
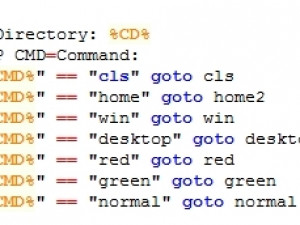
The command shell shortcuts allow the hacker to access certain directories, change the console colour, and make use of other typical command-line actions.
The attack doesn't stop there. In their attempt to capitalise on the attack, a Bitcoin miner is installed, to take advantage of every compromised computer. This software aims to use the victims' computer resources to generate the virtual currency, without them realising it.
Even if the victim realises his/her device has been breached and changes the credentials - the hacker is still able to gain access to the system. To enable Sticky Keys, the hacker enters the 'shift' key five times, allowing the cyber criminal to activate the backdoor once again.
Adaptive Defense 360, Panda Security's advanced cyber security solution, was capable of stopping this targeted attack, thanks to the continuous monitoring of the company's IT network, saving the organisation from serious financial and reputational harm. Business leaders need to recognise the need for advanced security, such as AD360, to protect their network from these kinds of attacks.
Share