Johannesburg, 22 Aug 2017
The world of malware and exploits has a long history, and anyone involved in this industry knows that we are at a tipping point. Threats continue to evolve, from the first viruses seen in the wild back in 1982, to the modern-day malware of today that's capable of spreading laterally in the blink of an eye.
We are in an arms race, and the traditional, legacy ways of dealing with these types of problems just doesn't cut it anymore. For the last few months I've been learning and playing with Palo Alto's Endpoint Protection solution, aptly entitled Traps. As someone who has worked in the network and cyber security industries over the last 20 years, I can tell you, it's a revolutionary approach to the problem of dealing with these types of attacks, says Juniper Ambassador Stefan Fouant. While the industry as a whole has focused on Antivirus (AV) mechanisms and more recently, Endpoint Detection and Response (EDR), Palo Alto is taking an altogether different approach; an approach that in my opinion will ultimately leave these legacy approaches in the dust.
Before taking a deep dive into Traps and what makes it so different, let's take a look at the landscape:
Antivirus (AV)
This is the home of traditional mainstays security vendors. But in the world of dealing with breaches and exploits, they are the dinosaurs, a dying breed. These security vendors to a large extent focus on using signature based methods to detect malware and exploits. Signature-based threat detection essentially works when the vendor creates a signature after a new virus or malware variant is discovered in the wild. This signature is then pushed out to customers in the form of a signature update.
The problem is, there are many ways to circumvent this, whether by using Do-it-Yourself malware encryptors, polymorphism, or generally any technique which can obfuscate the code and render it incapable of being matched against the signature database. Furthermore, cyber criminals are now taking the extra step of pre-scanning their malware against all the popular antivirus engines in order to ensure that it can effectively bypass these signature-based methods - affording the malware creator a much higher rate of success once they release it into the wild.
Endpoint detection and response (EDR)
EDR has been an area of technology that has been around for a few years now, and has typically been touted as something to address the shortcomings of traditional AV and augment its capabilities. According to Gartner, EDR is "an emerging security technology market created to satisfy the need for continuous detection and response to advanced threats - most notably to significantly improve security monitoring, threat detection and incident response capabilities." And while EDR certainly has a leg up when compared to legacy AV, the problem with this approach should be readily apparent.
As you can see from Gartner's definition above, most EDR vendors are focused on identifying Indicators of Compromise (IOCs) - AFTER a breach has occurred. So, while we can use this information to isolate and remediate machines which have been compromised, the fact remains that we are only doing so once a breach has occurred.
Another major shortfall of many of the existing EDR solutions is that many of them only focus on malware detection, but do very little in the area of exploits. So, this is a solution that has significant gaps when developing a defence-in-depth approach in the overall attack kill-chain life cycle.
Traps is a game changer
Traps is prevention focused. In terms of a comprehensive security posture, preventing threats should always trump detecting them. Detection and response is a secondary goal in relation to prevention. As most EDR approaches are really about detecting threats after a compromise has occurred, one really has to ask to what degree does this move our security posture forward? With the way most threats spreads laterally, by the time we've identified a compromised machine it has often already spread beyond our control. With gigabit speed networks common to the desktop today, and with the pervasive use of e-mail, social media and other distribution channels, an infected machine has the ability to spread in an exponential manner throughout an environment.
With its focus on threat prevention, Traps is more in line with traditional AV, in that the idea is to prevent the threat rather than identify it after the fact. But where AV falls short, Traps shines - they both focus on prevention, but Traps does so in a way that is much more scalable, and also addresses the lack of visibility into evolving and polymorphic threats that make them opaque to AV.
A focus on intelligent prevention is the only sustainable and scalable way to deal with malware and exploits.
How does Traps work?
Traps doesn't rely on signatures to accomplish its goals. Signature based methods require prior knowledge of weaponised exploits, and requires quite a large database of signatures to reside on the protected machine, consuming large amounts of disk space and memory. This technique doesn't scale as the number of threats continues to grow over time. Instead, Traps focuses on the smaller number of techniques that are commonly used, and with this approach it can identify threats without requiring any type of signature database. This also eliminates the need for constant updates, and translates into much smaller CPU and memory requirements on protected endpoints. The footprint is small! Really small. In my evaluation, it used a negligible amount of memory and disk space, rendering it virtually invisible in terms of its overall footprint.
Traps combines multiple prevention methods and also supports multiple purpose-built techniques per method, more akin to a defence-in-depth approach and attempts to prevent attacks at multiple stages of the attack kill-chain cycle. This approach allows for a very high rate of success as there are multiple places where malware and exploits can be prevented. If an attack happens to bypass one mechanism, there are multiple other stages where Traps can prevent the attack from furthering.
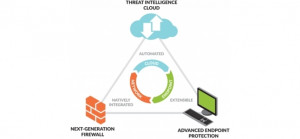
In addition to prevention of known attack vectors, any successful solution must also be able to detect unknown/zero-day malware and exploits. And this is where the real power of Traps exists - with its integration of a threat intelligence cloud that can identify zero-day threats, and automatically convert this intelligence into effective prevention techniques.
In Palo speak, we call this Wildfire - Wildfire is Palo's cloud-based sandbox environment which uses machine learning algorithms to identify these zero-day attacks. Wildfire has over a billion samples collected in the wild, and millions more are submitted every day on behalf of Palo's large installed base of customers.
An interesting thing to note is Palo takes all the threat information received in Wildfire and also submits it to the top AV vendors to compare efficacy of their solution to these other solutions. According to Palo, only 37.5% of threat samples submitted to Wildfire are detected by the top six AV vendors, which is direct evidence showing how ineffective these signature-based methods have become.
One of the strongest business cases for Traps is that it breathes new life into legacy operating systems that are end-of-life and no longer supported. If you are in a situation where upgrading your user desktops is just not feasible, and you are concerned that these systems may be vulnerable due to a lack of new security patches, Traps gives you a way to protect these systems long after they are no longer supported. With its multi-method prevention techniques and integration with Wildfire, you can rest assured these legacy systems will be protected from security vulnerabilities.
Traps is part of a larger ecosystem
At the end of the day, Traps integration with Wildfire is much more than just another sandbox solution - it's a powerful threat intelligence cloud that is shared amongst all of Palo's security products. It's the ultimate realisation of machine learning and security automation... and leverages the huge installed base of Palo's customers.
We can begin to see the real benefit when we look at the totality of Palo's overall security platform, especially when compared to other traditional AV and EDR vendors. The benefit of this security platform cannot be understated. Customers using the Traps solution benefit from the large installed base of customers who are also using Wildfire, gaining benefit not only from their own submissions but everyone else's as well. Furthermore, when coupled with Palo's Next-Gen Firewall solution, samples submitted here can also be leveraged. And when combined in this manner, the Next-Gen Firewall offers a whole host of other protections - application-level firewalling, network based attacks, URL filtering, anti-spyware, etc.
Is Traps the end of traditional AV and EDR?
I would state with an emphatic yes, Traps does indeed spell impending doom for the traditional AV and EDR market with its revolutionary new approach towards dealing with threats. It may not happen overnight, but I expect Traps to continue to gain traction and headway and eventually own a sizable chunk of the Endpoint market share. Coupled with its integration with the overarching Palo security platform, there are further benefits to be realized that can't similarly be offered by other vendors in the EDR space.
Clearly in this case, the whole is larger than the sum of its parts.
Original article published on http://www.shortestpathfirst.net/
Author: Stefan Fouant
Stefan Fouant brings over 18 years of experience in the service provider and network security industries as both a trusted advisor as well as a thought leader. Most recently, Fouant worked at Juniper Networks as a routing and security expert assisting large Tier 1 carriers. His background includes work at Verizon where he was responsible for launching one of the first large-scale cloud-enabled DDOS mitigation and detection services and also work at Neustar/UltraDNS where he was responsible for building out their layered DDOS response mechanisms, laying the groundwork for Neustar's DDOS mitigation service offerings. Most recently during his time at Corero, he has authored drafts within the IETF relating to standardised signalling of coordinated DDOS attack filtering and mitigation mechanisms. He holds several patents in the areas of DDOS Detection and Mitigation, as well as many industry certifications including CISSP, JNCIE-SP, JNCIE-ENT, and JNCIE-SEC. He was the first person in the world to achieve all three expert level Juniper certifications and was a technical editor of the book "Juniper MX Series" by O'Reilly.
Share