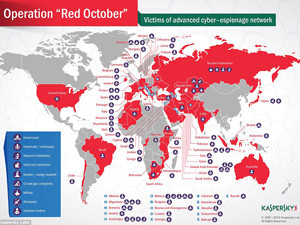
A high-level cyber-espionage campaign is believed to have infiltrated over 1 000 computers at diplomatic and government agencies.
Estimated to have been around for five years, the campaign has stolen terabytes of data from mobile devices, computer systems and network equipment, says Kaspersky Lab.
The company's researchers have spent several months analysing this malware, which it says targets specific organisations, mostly in Eastern Europe, former USSR members and countries in Central Asia, and to a lesser extent countries in Western Europe and North America.
Dubbed "Rocra", short for "Red October", the campaign remains active, with data being sent to multiple command-and-control (C&C) servers, through a configuration that Kaspersky says rivals the infrastructure of the notorious Flame malware in its complexity.
The attack's platform is unique, and features a multifunctional framework that can quickly extend the malware's intelligence-gathering features. It is resistant to attempts to take over the C&C servers, and permits the attacker to recover access to infected machines using alternative communication channels.
Registration data used for the purchase of C&C domain names and portable executable timestamps from collected executables suggest these attacks date as far back as May 2007, says the company.
The investigation further revealed the information harvested from infected networks is reused in later attacks.
"For example, stolen credentials were compiled in a list and used when the attackers needed to guess passwords and network credentials in other locations. To control the network of infected machines, the attackers created more than 60 domain names and several server hosting locations in different countries (mainly Germany and Russia). The C&C infrastructure is actually a chain of servers working as proxies and hiding the location of the true -mothership - command and control server," says Kaspersky Lab.
Over and above traditional attack targets such as workstations, the system is capable of stealing data from mobile devices, dumping enterprise network equipment configuration, hijacking files from removable disk drives, stealing e-mail databases from local Outlook storage or remote POP/IMAP servers, and siphoning files from local network FTP servers.
Kaspersky says it has observed the use of at least three different exploits for previously known vulnerabilities: CVE-2009-3129 (MS Excel), CVE-2010-3333 (MS Word) and CVE-2012-0158 (MS Word). "The earliest known attacks used the exploit for MS Excel and took place in 2010 and 2011, while attacks targeting the MS Word vulnerabilities appeared in the summer of 2012.
"The exploits from the documents used in spear phishing were created by other attackers and employed during different cyber attacks against Tibetan activists, as well as military and energy sector targets in Asia. The only thing that was changed is the executable which was embedded in the document; the attackers replaced it with their own code."
The security firm believes the people behind the attacks are Russian-speaking, due to the registration data of the C&C servers and numerous artefacts left in executables of the malware.
"Currently, there is no evidence linking this with a nation-state sponsored attack. The information stolen by the attackers is obviously of the highest level and includes geopolitical data which can be used by nation states. Such information could be traded in the underground and sold to the highest bidder, which can be, of course, anywhere," concludes Kaspersky.
Share