Johannesburg, 09 May 2016

A disturbing trend has lately surfaced in both retail and wholesale grocery outlets, relating to the manipulation of till slips/invoices by certain individuals aimed at committing fraud.
Case study:
In the sample provided, the following scenario occurred: two customers corroborated and approached the checkout with their respective goods, and the first customer purchased a few items, while the second only purchased a single can of Lucky Star Pilchards in Chili Sauce, for R6; the goods were paid for, and the respective invoices were issued.

The can of fish was then added to the same bag as the other goods, and only the one invoice was presented to the security check, while the other invoice was held as backup should they fail the security check. In this particular case, they passed the security check, which means only one invoice was cancelled. The invoice for the pilchards was then taken to a nearby facility (often inside a vehicle) where the invoice was manipulated to display different stock quantities and values, and then reprinted.
The forged receipt was then taken back to the store, and the quantity of stock on the new false receipt was collected, but not taken to a cashier, but rather straight to the security checkpoint.
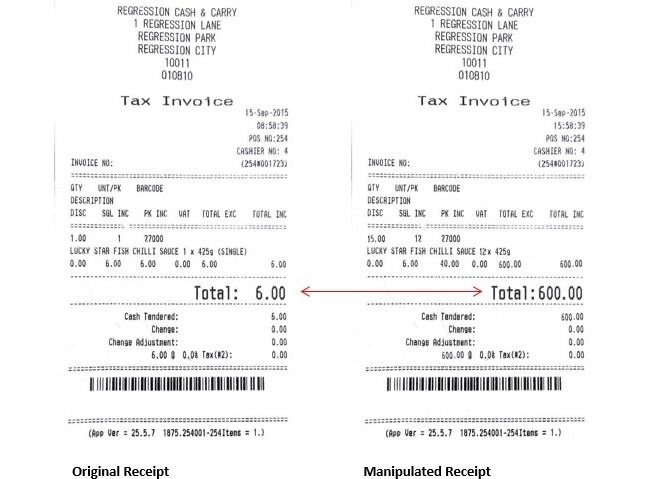
An analysis of the forged till slip reveals the following:
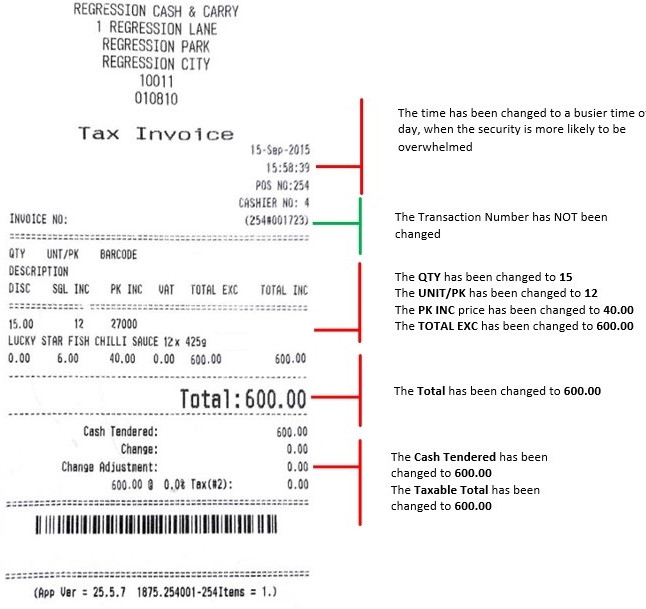
Methods of prevention:
Firstly, in order to overcome this phenomenon from occurring, it is possible to use the embedded inverted slip layout. This slip layout allows the store to print slips where the transaction-specific details are printed inverted, ie, on a solid black background. This makes it significantly more difficult to manipulate the receipt, but can still be done by a skilled forger.

Alternatively, Arch Retail Systems, a leading supplier of integrated retail management solutions, has developed Arch Mobile, a software solution run on a handheld scanner. Arch Mobile is used to scan receipts that have been issued by the cash registers at the security checkpoint before allowing the clients to exit the store. All that would be required is a receipt printer at the security point in addition to the Arch Mobile device. Arch is configured with a predetermined timeout for every issued receipt, eg, 10 minutes, which will force a new receipt to be printed at the security checkpoint if the timeout is exceeded. Once a new receipt is printed, the security officer can verify the new receipt with the customer's goods. Arch will store every transaction that has been generated, but will not permit a transaction to be scanned twice by Arch Mobile. Arch Retail developed this defence mechanism for a leading retailer group of theirs, after the described scam above was discovered.
Says David Geldenhuys, Marketing Executive Officer at Arch Retail Systems: "Retail management software faces many challenges in an ever-changing trading environment, to ensure fraud by both internal staff and customers, are minimised. The creativity of the criminal has no boundaries."
Share