Johannesburg, 18 May 2017
Forcepoint Security Labs has observed a major malicious e-mail campaign from the Necurs botnet spreading a new ransomware, which appears to call itself 'Jaff', peaking within its telemetry at nearly 5 million e-mails per hour.
The e-mails sent by this campaign may look spartan to the professional eye, but, as ever, the human point of interaction with systems is the most vulnerable: by potentially reaching so many individuals, campaigns such as this can - and do - succeed in infecting people.
Add to this a ransom of 1.79 bitcoins (approximately $3 300 at the time of the campaign) and the potential 'value' of the campaign is significant.
Analysis
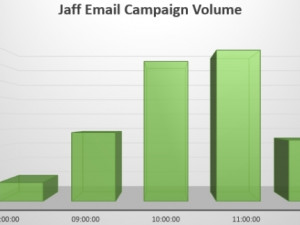
The campaign started just before 9am BST and had largely peaked by 1pm BST. During this short period, over 13 million e-mails were recorded and blocked by the Forcepoint systems. The graph below shows the hourly volumes recorded:
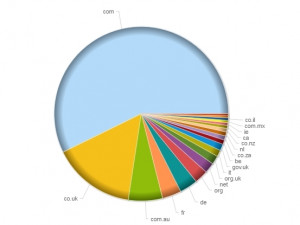
The campaign has a global scope: the graph below shows the top 20 recipient TLDs recorded within the telemetry. Perhaps unsurprisingly, .com domains make up the majority of the recipients recorded.
However, organisations in Ireland, Israel, Belgium, the Netherlands, Italy, Germany, France, Mexico and Australia also received a significant volume of malicious e-mail during this campaign. Further down the list, TLDs for countries such as Sri Lanka, Peru and Costa Rica were recorded, highlighting the breadth of this campaign.
The campaign theme is a fake document with the following e-mail subject format:
PDF_{four or more digits}
Scan_{four or more digits}
File_{four or more digits}
Copy_{four or more digits}
Document_{four or more digits}
Receipt to print
A screenshot of one of the malicious e-mails is shown below:
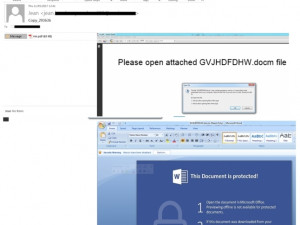
The attached PDF contains an embedded DOCM file with a malicious Macro script. This script will then download and execute the Jaff ransomware.
Possible ties with Locky
Jaff targets 423 file extensions. A complete list of these is provided at the end of this blog. It is capable of offline encryption without dependency on a command and control server. Once a file is encrypted, the '.jaff' file extension is appended.
In every affected folder, the ransom notes 'ReadMe.bmp', 'ReadMe.html' and 'ReadMe.txt' are dropped, while the desktop background of the infected system is also replaced. All of these components contain a message similar to the following:
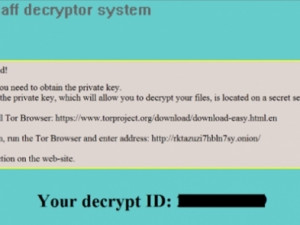
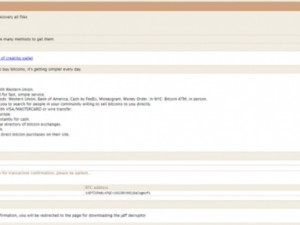
Meanwhile, there are a few indicators of a possible association between Jaff and the infamous Locky ransomware. For starters, both Jaff and Locky are spread by the Necurs botnet. Additionally, the Tor-based payment sites for both families resemble each other:
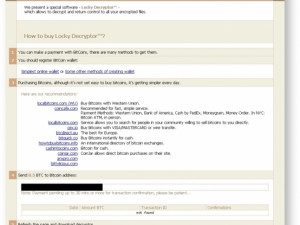
While the code behind Jaff is less sophisticated than Locky's, it attempts to delete itself if the local language of the machine is 'LANG_RUSSIAN' (0x19). Locky is known to implement a similar filtering:
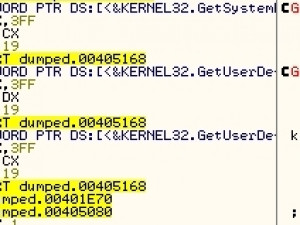
Finally, Jaff attempts to connect to the C2 server fkksjobnn43[.]org, which is hard-coded in its code. This is a known Locky domain.
Protection statement
Forcepoint customers are protected against this threat via TRITON ACE at the following stages of attack:
* Stage 2 (Lure) - Malicious e-mails associated with this attack are identified and blocked.
* Stage 5 (Dropper File) - Jaff variants are prevented from being downloaded.
* Stage 6 (Call Home) - Attempts by Jaff to contact its C&C server are blocked.
Conclusion
It's easy to be dismissive of broad-reach e-mail campaigns such as this, and focus on the more 'glamorous' world of spearphishing. The e-mails sent by this campaign may look spartan to the professional eye, but, as ever, the human point is the weak point: by potentially reaching so many people, campaigns such as this can - and do - succeed in infecting people.
This broad scope, coupled with low anti-virus detection rates at the time of the campaign, once again highlights the necessity of defence-in-depth.

At the time of writing, it is unclear if Jaff's links with Locky extend beyond the visual structure of the URLs and documents employed. What is clear, given the volume of messages sent, is that the actors behind the campaign have expended significant resources on making such a grand entrance. With the high ransom value suggesting the perpetrators of this campaign intend to recoup their costs, it would be surprising if Jaff fades from the limelight as suddenly.
Please note: this post is not related to the global WannaCry outbreak on Friday 12 May 2017. For ongoing updates on WannaCry, please see Forcepoint's blog post at https://blogs.forcepoint.com/security-labs/wannacry-ransomware-worm-targets-unpatched-systems
Share