ITWeb’s 2019 Information Security Survey, carried out in association with VMWare, indicates that IT security preparedness is improving in South Africa – with business-driven compliance, risk and internal threats among the drivers for this.
Revealing the findings of the second annual survey at the ITWeb Security Summit 2019 in Johannesburg, Ian Jansen van Rensburg, lead technologist & senior systems engineering manager at VMware, said South African enterprise security was maturing, with cyber risk promoted into the enterprise risk register by 58% of respondents. There are more formal cyber security policies in place, and there has been a marked improvement in the prevention of loss or leakage of confidential data (13% in 2019, down from 44% in 2018).
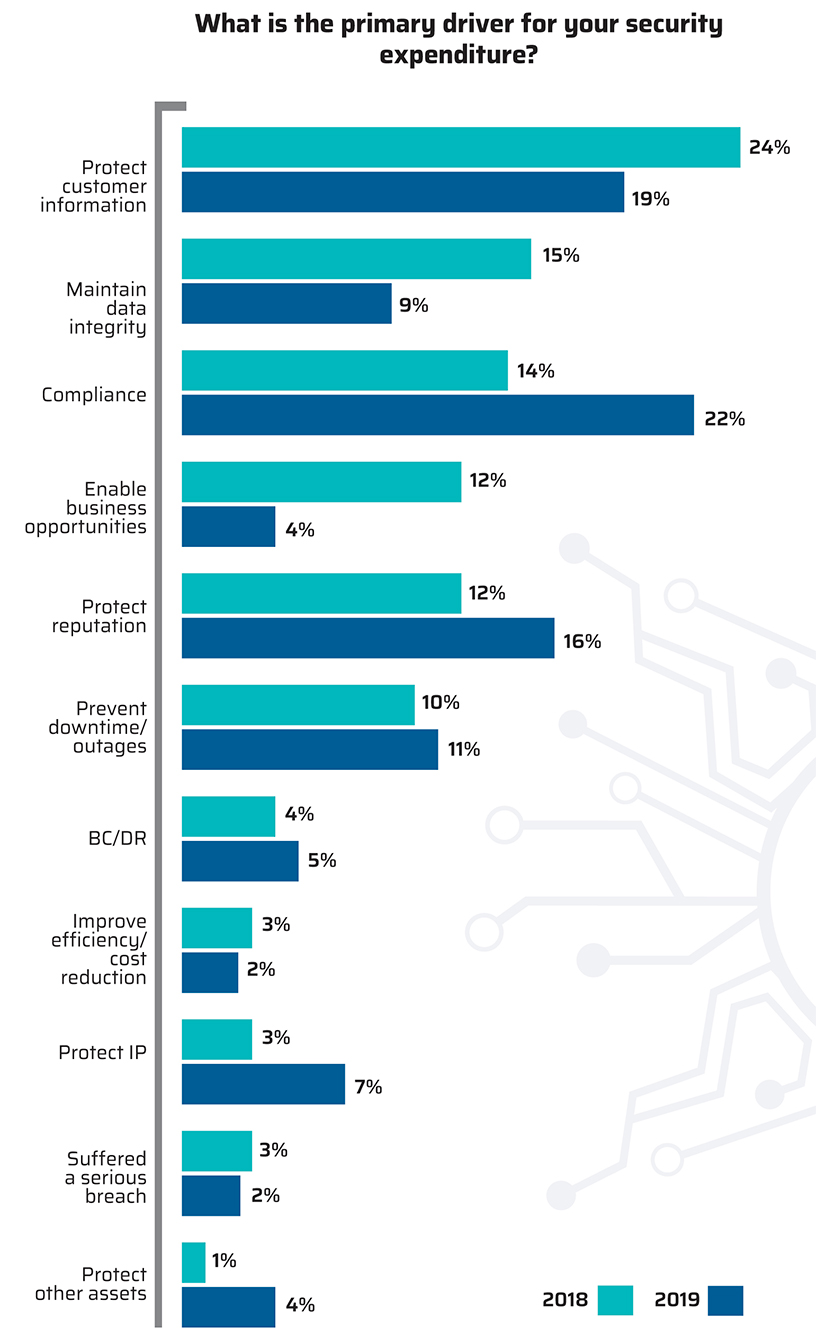
Business-driven compliance demands, including the need to meet POPI and GDPR requirements, were cited by 22% of respondents as a primary reason for IT security spend this year, compared with only 14% last year. Other top drivers of IT security spend remain protecting customer information (19%), protecting the enterprise’s reputation (16%) and preventing downtime and outages (11%).
There was an increase in respondents’ reported maturity levels, with a drop in the number of organisations saying they were at the low end of maturity and a significant increase in the number of those reporting they were at a mid-range maturity level (from 32% in 2018 to 49% in 2019).
“So companies are spending quite a lot of money on keeping the bad guys out,” said Jansen van Rensburg, “But it’s particularly interesting to see that 57% of respondents were victims of a phishing attack in the past year, and just under 28% have experienced internal, staff-related breaches.”
Insider attacks were considered the top security risk, with 29% of respondents citing that as their greatest concern, followed by uncontrolled portable devices (14%) and e-mail viruses (13%).
He noted that high-profile attacks highlighted during the ITWeb Security Summit, including the Gautrain Management Agency breach, illustrated that insider attacks could be particularly devastating.
“Companies are fairly good at protecting the ‘crown jewels’ with edge protection, but once an attacker is inside the network, they can do whatever they want,” he said. “Security today means more than just keeping the bad guys out of the network. We need to rethink the way security is done, and move to software-defined approaches.”
To access the key findings report in PDF format follow this link.