Sensitive business information, customer details, financials, transactions and product information all form part of important data in organisations and is the lifeblood of every business. But, how much control do businesses have over their data? Do they know where it is, is it secure, and what are the risks to the business if that data is lost or compromised?
"These are questions that every business should know the answers to," says Charl Ueckermann, CEO at AVeS Cyber Security. Protecting data should be prioritised as part of the business's sustainability strategy because when data is compromised or lost, it is a major threat to business continuity. Just ask any business that cannot recover their information because backups weren't carried out before a server crash.
"Some data is also confidential. Not only do you not want to lose it, but you don't want others to be able to access it without authorisation. This could put you or your business at risk of non-compliance with legislation that is in place to protect sensitive information and people's privacy. Information regulators can impose hefty fines on organisations that don't take the necessary measures to protect the information they collect, process and store.
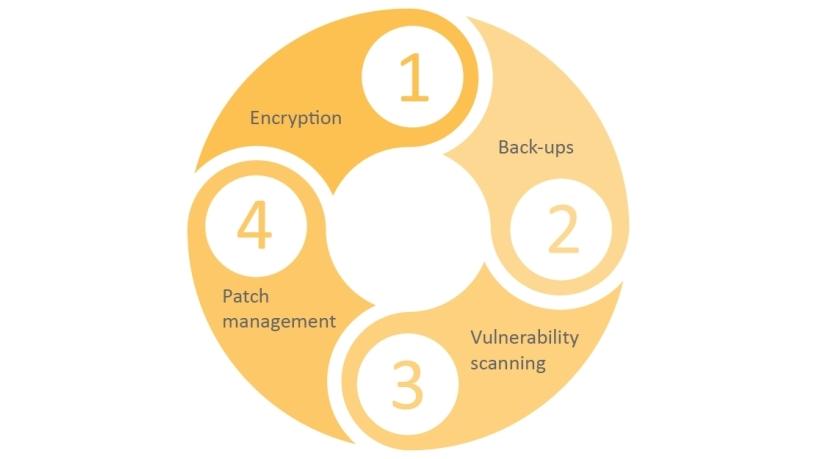
"To effectively secure data and prevent data loss," says Ueckermann, "companies need to encrypt, backup, scan for vulnerabilities and make sure that patch management happens."
The first step, though, is to know where the data lies. Nowadays, data exists on servers, endpoints, mobile devices, on the Internet and even copiers and printers. It resides in documents, in e-mails, in applications and peripheral devices like USBs. Of course, not all of this information is equally critical, so classifying data, separating confidential from non-confidential data, is the next step.
"Confidential information should be sorted from non-confidential data for data loss protection and backup strategies to be appropriately targeted. This way, protection can be data-centric, which means it is applied to the data itself rather than the device, network or user account. When protection is at a data level, sensitive information can be encrypted before it leaves the network or is transferred to an approved device.
"Furthermore, when data loss prevention is data-centric, companies can leverage technologies to block unauthorised access to and use of certain types of information. Users can also be warned when they are about to do something with the data that could put it at risk," explains Ueckermann.
Regular vulnerability scans of the IT infrastructure, including the network, firewalls and endpoints, are also necessary to protect it from data breaches or ransomware infections as a result of criminals exploiting vulnerabilities within the software. Vulnerability and patch management in security software, for instance, analyse the infrastructure to detect and eliminate vulnerabilities in operating systems and applications. Detected problems are ranked by severity and "fix" recommendations are provided.
"This gives companies a picture of their data security standpoint and identifies where the potential vulnerabilities are that could pose a risk to data security. Oftentimes, security gaps are left open, because security updates have not been applied or patch management has not been done. Unpatched vulnerabilities, especially those in popular applications, can pose a significant threat to business's IT security," says Ueckermann.
The depth of the core components for protecting against data loss, namely encryption, backups, vulnerability scanning and patch management, will depend on an organisation's specific security requirements and where they are on their IT security journey. Then there are the nuts and bolts that keep data secure, such as endpoint security, mobile security, and firewalls, among others.
"Certainly, some businesses are way ahead of others regarding data loss protection. While some have reached a higher level of maturity, where IT is considered a strategic partner to the business and there is a proactive analysis of the security posture and trends, as well as management of risks, others have yet to determine which data is important to them and implement interventions to protect it."
According to Ueckermann, a holistic approach to data protection for the average business can be found in solutions like Kaspersky Endpoint Security for Business Advanced. It is an innovative platform, which provides security and management capabilities of all endpoints in progressive tiers of protection. It features award-winning anti-malware, data encryption, mobile threat defence, vulnerability and patch management, as well as device and application control tools. The product allows managing up to 100 000 endpoints through a single server installation and through a single management console.
For organisations with a high security agenda, mechanisms must be built into all layers of their infrastructure and, depending on the specific environment and business requirements, specialised software is necessary, such as intrusion protection technologies.
"If you are not sure where your company is on the continuum, and you are unable to answer questions like, 'where is my data?' or 'is my sensitive information protected against unauthorised access?' then it is time to speak to a specialist provider that can guide you on understanding and prioritising data security risks before implementing the most appropriate interventions to stop data loss," concludes Ueckermann.
Share
AVeS Cyber Security
AVeS Cyber Security is a specialist IT governance and architectural services consultancy that combines expert knowledge and services with leading technology products to provide comprehensive information security and advanced IT infrastructure solutions. Over the past 20 years, AVeS Cyber Security has strategically honed its solutions and services to help southern African businesses future-proof their IT environments against the constantly evolving threat landscape, while achieving their digital transformation aspirations. The company offers a leading portfolio of professional services, products and training in security, infrastructure and governance solutions. In 2017, the company won nine awards from some of the world's top technology vendors, indicating competency, strength, innovation and robustness in an industry that is fast growing in complexity due to evolving challenges such as ransomware, advanced targeted attacks and the Internet of things.
Editorial contacts