
Cloud security? How does one secure a cloud?
With all the jargon, threats and ever-changing technology, securely tying down your digital assets may appear to be almost as impossible as trying to secure the real thing... I mean, an actual cloud that floats in the sky, rains and shoots out the occasional lightning bolt. As convenient and "virtual" as the concept of a digital cloud in 2018 sounds, your precious data still needs to reside somewhere, and that somewhere, like anything in life, is still prone to theft, loss or attack. So, how does one secure a cloud?
Cloud security is basically a broad set of policies, technologies, and controls used to protect your data, applications, and the connected infrastructure of cloud computing. It is a sub-domain of computer security, network security, and, more broadly, information security. It's certainly possible to keep your personal and company data on cloud servers secure, but cyber threats are evolving and cloud servers are a becoming a major target. Organisations and individuals are increasingly migrating to the cloud to process their IT resources. Gartner predicts that cloud data centres will process 92% of workloads by 2020.
Keep these top cloud security threats in mind, and you'll have the right mindset for properly securing your personal and business's valuable data...
Top cloud security threats in 2018
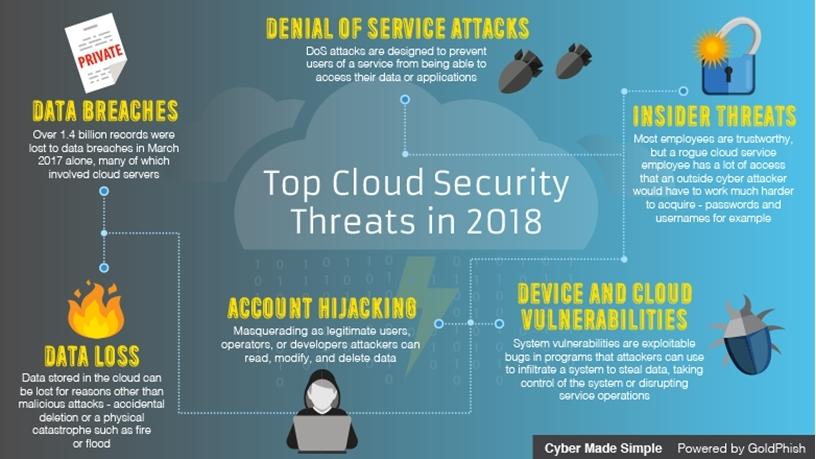
1. Data breaches
A data breach might be the primary objective of a targeted attack or simply the result of human error, application vulnerabilities, or poor security practices. It might involve any kind of information that was not intended for public release, including personal health information, financial information, personally identifiable information, trade secrets, and intellectual property. The risk of a data breach is not unique to cloud computing, but it consistently ranks as a top concern for cloud customers. 2017 for example was a huge year for data breaches. There were 143 million ordinary people affected by September's Equifax breach, and in May 2017, OneLogin, which provides identity management and single sign-on capabilities for the cloud services of over 2 000 companies worldwide, discovered a major data breach. Over 1.4 billion records were lost to data breaches in March 2017 alone, many of which involved cloud servers.
2. Data loss
Data stored in the cloud can be lost for reasons other than malicious attacks. An accidental deletion by the cloud service provider, or a physical catastrophe such as a fire, flood or earthquake, can lead to the permanent loss of customer data, unless the provider or cloud consumer takes adequate measures to backup data. Threats to your cloud data don't always look like malicious characters in the shadows wearing hoodies. It's easy to underestimate the risk of something bad happening to your data due to an innocent mistake and because it's so "virtual", so keep multiple backups at physical sites at different geographic locations.
3. Insider threats
Insider threats to cloud security are also underestimated. Most employees are trustworthy, but a rogue cloud service employee has a lot of access that an outside cyber attacker would have to work much harder to acquire. When an organisation elects to store data or host applications on the public cloud, it loses its ability to have physical access to the servers hosting its information. As a result, potentially sensitive data is at risk from insider attacks. According to a recent CSA report, insider attacks are the sixth biggest threat in cloud computing. Therefore, cloud service providers must ensure that thorough background checks are conducted for employees who have physical access to the servers in the data centre.
4. Denial of service attacks
Denial of service (DOS) attacks are pretty simple for cyber attackers to execute, especially if they have control of a botnet. DOS attacks are designed to prevent users of a service from being able to access their data or applications. By forcing the targeted cloud service to consume inordinate amounts of finite system resources such as processor power, memory, disk space, or network bandwidth, attackers can cause a system slowdown and leave all legitimate service users without access to services. DDOS as a service (distributed denial of service) is also growing in popularity on the 'dark Web'. Now attackers don't need know-how or their own bots; all they have to do is transfer some of their crypto-currency in order to buy a dark Web service. An effective DDOS attack on a cloud service gives cyber attackers the time they need to execute other types of cyber attacks without getting caught.
5. Account hijacking
Account or service hijacking is not new, but cloud services add a new threat to the landscape. Masquerading as legitimate users, operators, or developers, attackers can read, modify and delete data; issue control plane and management functions; snoop on data in transit or release malicious software that appears to originate from a legitimate source.
6. Spectre, Meltdown and others: device and cloud vulnerabilities
Intel processors are having a Meltdown while AMD and ARM are being attacked by a Spectre. Is a James Bond villain making our computers freak out? No, it's a new vulnerability found within these processors that affects Windows PCs, Linux, Mac, and even Android phones. System vulnerabilities are exploitable bugs in programs that attackers can use to infiltrate a system to steal data, taking control of the system or disrupting service operations. At the beginning of the year (2018), everyone was talking about "Meltdown" and "Spectre" that potentially exposed data in everything from servers and desktops to tablets and smartphones. The flaws, which impacted the chips in many popular devices, allowed hackers to inconspicuously manipulate a common efficiency technique used to speed data processing. As a result, chip manufacturers and software makers scrambled to issue patches and work out the performance sluggishness that came along with blocking the risky optimisations.
At the same time, though, a larger concern was also looming: Spectre and Meltdown represented a whole new class of attack, and researchers anticipated they would eventually discover other, similar, flaws. In May this year (2018), researchers from Microsoft and Google's Project Zero disclosed a new, related vulnerability known as Speculative Store Bypass Variant 4 (Meltdown and Spectre collectively make up variants 1-3) that impacts Intel, AMD, and ARM processors. If exploited, an attacker could abuse the bug to access data that is meant to be stored out of reach.
Microsoft says the risk to users from this bug is "low," and Intel notes there is no evidence that the flaw is being used by hackers. But, it is a major cause for concern; what other "bugs" or "back doors" into our devices and cloud-stored data might there be? Time will only tell.
For now, though, prevent hackers from taking advantage of Meltdown, Spectre and others yet to be named:
Make sure to keep all the software on your computer updated, including Web browsers. Keep Flash updated as well.
Then run security software to be sure you don't have any unwanted or malicious software on your system.
Finally, be on the lookout for phishing e-mails. A hacker could use this to trick you into letting their malicious code onto your system.
CybACADEMY courses, powered by GoldPhish, educate employees on the cyber risk and help build a more secure organisation with awareness training.
Our free campaign is aimed at helping smaller businesses get one step ahead of the cyber criminals with free awareness training.
Want more information on products and services provided by GoldPhish? E-mail info@goldphish.com.
Share
Editorial contacts