
All organisations strive to have their IT security infrastructure designed effectively, to enable key business activities, while simultaneously ensuring the highest levels of reliability and accessibility. In most cases, a bottom-up approach is taken, predominantly due to the large number of vendors in this space, creating a focus on trying to protect against every conceivable threat.
Organisations are rarely able to visualise the key IT security technology domains, and where they fit into an environment in order to achieve optimal governance, minimal risk and adherence to compliance. Instead of organisations becoming more relevant and agile in their response to security challenges, increased complexity is created which can overwhelm IT security teams.
The challenge is compounded by patient attackers, sophisticated advanced threats, and the increasing use of cloud and mobile technologies, which expand the potential attack surface. "Our innovative defence-in-depth Security Framework helps customers define their IT security vision and subsequently their strategic objectives, top-down. Customers and partners can now be confident that they can comprehensively cover their IT security needs, end-to-end, from the user to the network to the application, and finally, to the data," said Wayne Donnelly, South Africa's Country Manager at StarLink.
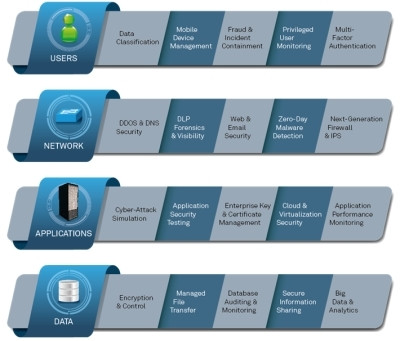
Achieving compliance and protecting against cyber attacks still continue to be the primary two IT security drivers that shape the industry, and over the last few years, significant vendor consolidation has taken place, both in terms of acquisitions and mergers, as well as development of strategic partners and alliances. This has created an ecosystem of out-of-the-box integration, as well as, a landscape where IT security requirements cannot be addressed with point products, but instead multiple technologies that work side by side.
Donnelly further commented: "StarLink's portfolio has evolved into a uniquely structured Solutions Lifecycle consisting of access control, vulnerability management, advanced threat protection and secure mobility. Each of these solutions comprises multiple vendors' core competencies, and feed into each other, giving customers the ability to quickly understand their IT security gaps, and set priorities accordingly, starting from implementing critical controls, to verification of those controls, to zero-day malware protection, to sensitive data consumption, and then back around again."
IT security challenges can no longer be addressed by point products. Such products typically fail to provide a comprehensive, integrated picture of the threat landscape, each returning its own results but missing the opportunity to put results into context, falling short of enterprise-wide insights, and increasing the complexity of managing the IT security platform. At the root of the problem is the fact that most point solutions operate in silos; they typically do not integrate with other products in the security infrastructure. It becomes difficult for the security team to see through the noise and understand where real threats and real vulnerabilities are hidden.
An integrated approach requires capabilities to achieve compliance, as well as to monitor for and prevent attacks on the network, on the endpoint and across other IT assets, said Donnelly.
These detected security concerns must be investigated quickly, with tools that can integrate context from across the environment with the passing of security information, alerts and policies between security domains, he further commented. Once this analysis is complete, security gaps can be bridged, or remediated, and ongoing protection can be implemented. This methodology allows for faster, more effective identification and mitigation of potential security threats, as well as helping in the identification of behaviour anomalies, risk prioritisation, and increased visibility and control.
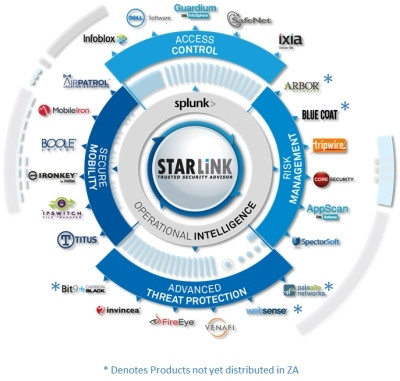
StarLink's approach to positioning its Solution Lifecycle is driven by a data-centric view and addressed with four simple leading questions. Donnelly believes that, firstly, we need to ask ourselves, 'Where is my sensitive data? Simply put, how do I control, identify, monitor, protect and analyse it?' The next question is, 'Is my sensitive data at risk? In other words, how do I detect potential attacks, visualise the attack, scan for vulnerabilities, validate and test the outcomes, assess the business impact, and finally, investigate all the activities associated with this?'
Thirdly, we ask, 'How can I protect my sensitive data? I need to defend my enterprise platform, next, enforce my controls and policies, then implement a trust model while maturing to solutions and technologies that protect me against next-generation malware and APTs. I then need to be able to contain any incidents, and once an acceptable level of sanity is achieved, I should baseline my environment.'
Finally, 'How do I share my sensitive data? I would want to classify it with minimal impact to the business, then I need to transfer it by adopting secure managed file transfer, and in the event of needing to move it, I need a secure way, such as encryption of devices where portable data is held. Next, I need to look at how to share my data via secure information sharing linked to rights management, and with the hyper growth on mobile devices, I need to be able to manage and secure my mobile devices, mobile applications and mobile content. Finally, I need the flexibility to apply my security policies to these devices based on their locations.'
For a more in-depth view about StarLink's Security Framework and Solutions Lifecycle approach, visit www.starlinkme.net or contact StarLink +27 (11) 510 0000.
Share
Editorial contacts