Network security can be an intimidating discipline for most organisations. The threat landscape is becoming increasingly dangerous, as malicious actors focus their energy on developing sophisticated, targeted attacks.
At the same time, the anywhere, anytime mobile workforce, digital workplace transformation, IOT applications, and the move to the cloud are increasing the size and complexity of IT infrastructures and their associated attack surfaces.
What is the state of network security today and what can be done to improve it?
This paper concludes:
* New business objectives are making network security more difficult. ESG research reveals that most organisations believe network security is getting more complex every year. Why? More on-premises and cloud applications, devices, users and network traffic are increasing the attack surface, making it increasingly difficult to prevent, detect and respond to security incidents. The persistent cyber security skills shortage and ever-increasing sophistication and volume of threats and targeted attacks also compound the challenge.
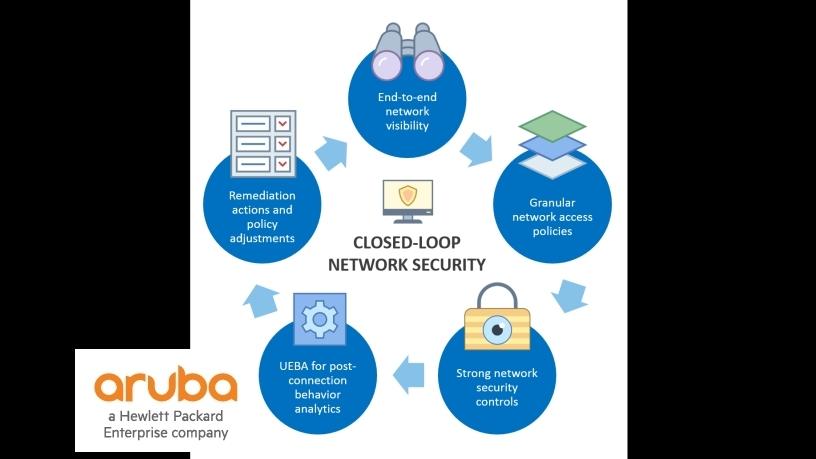
* CISOs must think in terms of "closed-loop" network security. Given the growing complexities of the network, security executives must focus on improving threat prevention, detection and response. This goal can be facilitated through a closed-loop approach to network security.
This strategy includes:
* Complete visibility of all devices connected to the network. IT needs to continuously monitor the network to provide the security team with an up-to-date inventory of every device and user on the network.
* Granular network access policies governing who gets access to network assets (ie, users and devices). With policy management, network access policies can be centrally enforced for all wired and wireless connections regardless of location, user, or device type. Applying the principle of least privilege, granular policies can ensure that access is granted to the minimum number of necessary resources. This helps to mitigate risk and reduces the attack surface as each device or user connects.
* Strong network security controls for policy enforcement. Network security policies must be enforced through tight integration between network access control and other security technologies, such as threat intelligence, endpoint management, IDS/IPSes, and firewalls, as well as network infrastructure, such as switches, routers, and wireless access points. Working together, all of these technologies can be used to develop and enforce security policies while providing the ability for policy adjustments based on changing threats and vulnerabilities.
* User and entity behavior analytics (UEBA) to monitor for post-connection suspicious/malicious behaviour emanating from users and devices. UEBA technology can be applied to help security analysts detect suspicious behaviour or patterns of anomalies after connections have been established. UEBA can also be used to process the millions of log entries generated by every device on the network, contextualise and enrich security telemetry, prioritise events, and greatly reduce false positives.
Share