
Security breach. Hacking. Cyber warfare. Industrial espionage. These make headlines across the world as any high profile Web site or social network accounts are breached.
One could think there are armies who deploy sophisticated technological weapons across the Internet, with missile-like-precision finding their intended target.
While this does happen, the arsenal of weapons that exists doesn't have to be so sophisticated. In fact, they are so common that anyone, with no programming skills at all, can now buy these systems online for a couple of dollars. This was one of the key underlying elements that speakers included in their presentations at the recent ITWeb Security Summit. Yes, there is an element of technological defences that need to be deployed at home and at work, but there is still one weak link that no technology can assist with - the human being.
We have been told countless times not to click on any e-mail that looks suspicious, and certainly not to click on links inside e-mails that ask us for usernames and passwords. Yet, every day, thousands of people do exactly that and then find themselves in hot water, as they realise they have fallen victim to cyber crime. This is kind of attack is known as phishing, and is a favourite tool among the attackers.
How does phishing work?
Phishing is based on a couple of components. The hacker purchases a mailing list of e-mail addresses; then the hacker creates an e-mail that mimics a popular Web site, such as LinkedIn or Facebook.
Inside this mass e-mail, there is an invitation to click on a link that takes the recipients to a "landing page", which is where they are asked to enter the sensitive information, such as usernames and passwords. This information is sent to the attacker and a "sorry we are offline - try again later" message is displayed to the user, so they simply switch off, thinking nothing of it.
Why does phishing work?
Phishing is successful as it is based on sheer numbers. Sending out millions of e-mails will result in some people revealing their information for hackers to do with as they please. There is even a market for selling active usernames and passwords.
What is spear phishing?
An advanced version of phishing is known as spear phishing. This is where the attacker targets specific sets of people, instead of a blanket mass mail. The attacker will create a Web page that is common to the selected group, eg, mimicking a specific banking site's Web page or a company Web mail login page, and then sending the mass mail to those specific people, such as those people with a .co.za in their e-mail, if the bank is in South Africa.
This kind of attack is successful as the recipient visually identifies with the Web site that s/he constantly accesses, and therefore doesn't think twice about logging in, thus revealing his/her sensitive information.
The spyware
As an added 'bonus', as part of the phishing attack, the attacker may wish to add spyware software that is installed on the recipient's computer. This is done by embedding the malicious code on the landing page and manipulating the victim to install the "software update" or "security patch".
This allows the attacker to access that computer via a backdoor that the software creates. The malicious software may also replicate itself on the network to other machines, and may even send keys pressed on the keyboard to the attacker (known as keyloggers).
The reactions
There are two typical reactions that people have when we hear about these attacks.
1. "I am safe, I have an anti-virus!" and 2. "Who would be so stupid to fall for this?"
The "I have an anti-virus" reaction is common, but unfortunately, this is not good enough. Even those people who are diligent and update their software regularly are still susceptible. There are many "services" on offer that for R600 will guarantee that an attacker's hacking code will bypass all the anti-virus systems. Even when there is an update, this service will develop the workaround for the code to work. You even get a service level agreement!

The "who would fall for this" question is something you can answer for yourself. thinkst has developed a tool called Phish5, which allows you to "attack" your own company and see if you are vulnerable to phishing attacks.
Simply sign up, add some members in your company, use the template to build your fake phishing e-mail, use the template to create a fake landing page, and launch your attack. You will be notified as soon as people fall victim - there are even graphs and reports.
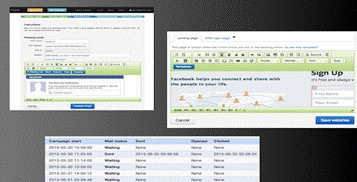
Phishing is just one tool in the hacker's arsenal, and falls under the bigger umbrella known as social engineering - the way attackers will manipulate people into helping them get the information they want.
No amount of technology can fully protect your business. There has to be constant training of the people using the system. Speaker after speaker after speaker confirmed this at the ITWeb Security Summit, repeating the same mantra: If your business has something worth stealing, chances are the hacker is already in. Only the "bad" hackers are caught, the "good" ones run a business - selling your information.

Share